Search Exchange
Search All Sites
Nagios Live Webinars
Let our experts show you how Nagios can help your organization.Login
Directory Tree
Directory
stefanlasiewski
bystefanlasiewski, April 27, 2016
This tool works, but it hasn't received an update since 2013.
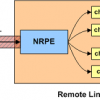
Functionally, NRPE can only handle a payload of 1024 bytes, which limits the amount of data that you can receive on your Nagios server. There have been a couple security reports with NRPE since the last release (See https://www.opsview.com/resources/blog/nagios-nrpe-security-vulnerability ), and it's not clear if Nagios.com ever patched their code in response to these reports.
Functionally, NRPE can only handle a payload of 1024 bytes, which limits the amount of data that you can receive on your Nagios server. There have been a couple security reports with NRPE since the last release (See https://www.opsview.com/resources/blog/nagios-nrpe-security-vulnerability ), and it's not clear if Nagios.com ever patched their code in response to these reports.
bystefanlasiewski, October 6, 2015
1 of 2 people found this review helpful
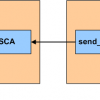
The NSCA addon has been ignored and neglected for years. For passive checks, try NRDP instead.
I can't imagine why NSCA is still a featured plugin on the Nagios Exchange when it hasn't received an update in over 3 years.
The NSCA addons work, but they are buggy, crash too often and will lead to false positives on your Nagios server.
The 2.9 branch and 2.7 branch are not compatible. The 2.7 branch is still in wide use due to these compatibility issues, but it hasn't received an update since 1997. The 2.9 branch hasn't received an update since 2012.
I can't imagine why NSCA is still a featured plugin on the Nagios Exchange when it hasn't received an update in over 3 years.
The NSCA addons work, but they are buggy, crash too often and will lead to false positives on your Nagios server.
The 2.9 branch and 2.7 branch are not compatible. The 2.7 branch is still in wide use due to these compatibility issues, but it hasn't received an update since 1997. The 2.9 branch hasn't received an update since 2012.
bystefanlasiewski, April 4, 2014
I'm pleased with this update but I had to modify the python code to replace the deprecated classes os.popen4 .
I wish these projects were on github so that we could contribute fixes.
I wish these projects were on github so that we could contribute fixes.
bystefanlasiewski, March 26, 2013
1 of 1 people found this review helpful
Seems pretty good, and the best out the ones that I have tested. However, the following requirement is confusing:
> If running on a 64-bit system, make sure you get
> the 64-bit 3ware utility tw_cli and name it
> tw_cli_64 as this is the name the plugin looks
> for on 64-bit systems.
It shouldn't matter if the utility is named either tw_cli or tw_cli_64, it will function the same. I don't understand why this script needs the file to be renamed to tw_cli_64, when 'tw_cli' works just fine. I pulled this part out of the script, as the required rename made our configuration management more complicated.
> If running on a 64-bit system, make sure you get
> the 64-bit 3ware utility tw_cli and name it
> tw_cli_64 as this is the name the plugin looks
> for on 64-bit systems.
It shouldn't matter if the utility is named either tw_cli or tw_cli_64, it will function the same. I don't understand why this script needs the file to be renamed to tw_cli_64, when 'tw_cli' works just fine. I pulled this part out of the script, as the required rename made our configuration management more complicated.
bystefanlasiewski, November 18, 2009
1 of 1 people found this review helpful
Nice simple check. The Perl code is readable.
The script provides options which let you specify the specific Controller and specific Unit.
I prefer to use NRPE, NSCA or check_by_ssh to check my remote hosts, and the built-in SSH seems redundant. This is just my preference.
I'm testing this on FreeBSD 7.2 (By changing the path) with a 3ware 9000 series. It seems to work fine. I'll probably use it on some CentOS 5.4 machines shortly.
Some issues:
1. I need to specify the specific Unit (e.g "check_3ware.pl --controller 0 --unit 1"), otherwise this script only checks Unit 0.
2. The script has a list of keywords for the WARNING and OK states. Anything else becomes CRITICAL. If the array shows a "DEGRADED" or OFFLINE message, this script will consider that a WARNING. Really, the script should specify OK, WARNING and CRITICAL states. Anything else should become UNKNOWN.
It's easy enough to change the OK and WARNING criteria by adding them to the @state_ok & @state_warning Perl arrays.
The script provides options which let you specify the specific Controller and specific Unit.
I prefer to use NRPE, NSCA or check_by_ssh to check my remote hosts, and the built-in SSH seems redundant. This is just my preference.
I'm testing this on FreeBSD 7.2 (By changing the path) with a 3ware 9000 series. It seems to work fine. I'll probably use it on some CentOS 5.4 machines shortly.
Some issues:
1. I need to specify the specific Unit (e.g "check_3ware.pl --controller 0 --unit 1"), otherwise this script only checks Unit 0.
2. The script has a list of keywords for the WARNING and OK states. Anything else becomes CRITICAL. If the array shows a "DEGRADED" or OFFLINE message, this script will consider that a WARNING. Really, the script should specify OK, WARNING and CRITICAL states. Anything else should become UNKNOWN.
It's easy enough to change the OK and WARNING criteria by adding them to the @state_ok & @state_warning Perl arrays.

 Directory
Directory New Listings
New Listings